The Future
Eli Mobile is the first Telco to officially include blockchain in its structure, but why limit it to Elisium and the NFT world? Eli Mobile is ready to bring blockchain as a structural element into the very concept of telecommunications.
CASE #1 ROAMING FRAUD PREVENTION
The cost of telecommunications fraud is estimated to be more than $38 billion per year. Thanks to some features of the blockchain it can be prevented in an effective and sustainable way.
Current situation - Roaming fraud occurs when a subscriber accesses HPMN (Home Public Mobile Network) resources via a VPNM (Visited Public Mobile Network) but the HPMN is unable to charge the subscriber for the services provided and is still obliged to pay the VPNM for roaming services.
Roaming fraud exploits two characteristics:
Longer detection time: fraud occurs when the subscriber is on a different network from the HPMN, more time is needed to detect it owing to delays in data exchange between the VPMN and the HPMN.
Longer response time: owing to the lack of control over the systems where the fraud occurred, the response time is longer than if the fraud had occurred in a system owned by the HPMN.
The blockchain solution - The permission logic, typical of the blockchain, can be adopted between a pair of telephone operators with a roaming agreement, to achieve instant verification and smart contract compliant payments.
The roaming agreement is implemented between the HPMN and the VPMN as a smart contract that is activated when a transaction containing CDR (Call Detail Records) is transmitted onto the blockchain network. Nodes, designated by both operators, act as miners to verify the veracity of each transaction and whenever a subscriber triggers an event in a transit network, the VPMN transmits the CDR information as a transaction to the HPMN. This data triggers the smart contract and the terms of the agreement are executed, the HPMN can automatically calculate the billing amount based on the services rendered and send this information back to the VPMN.
Benefits:
Reduced fraud based on the subscribers’ IDs.
Easier and faster device identification on the move, thanks to the shared database that has the device's public key information and history.
Providing identity to devices in M2M or IoT environment, without having to insert physical SIM cards.
Eliminating the cost of producing and distributing physical SIM cards.
USE #2 - IDENTITY VERIFICATION
Current situation - Currently, registering with a provider requires proving one's identity through physical or digital documents, handing over large amounts of personal information, even if the provider does not need it, creating different username/password combinations or using third-party provider services (such as Google and Facebook Sign On). The identity and authentication system therefore has many critical issues, including a lack of convenience (too many username/password combinations) and security (personal data shared by third parties).
The blockchain solution - A telco, owing to the amount of sensitive subscriber data, can play an important role in this area by creating a centralized user identity management for its services and offer it to its partners as well. Through blockchain technology, identity authentication is shared across different devices, applications and organizations to help the user/subscriber maintain one or more identities on each platform.
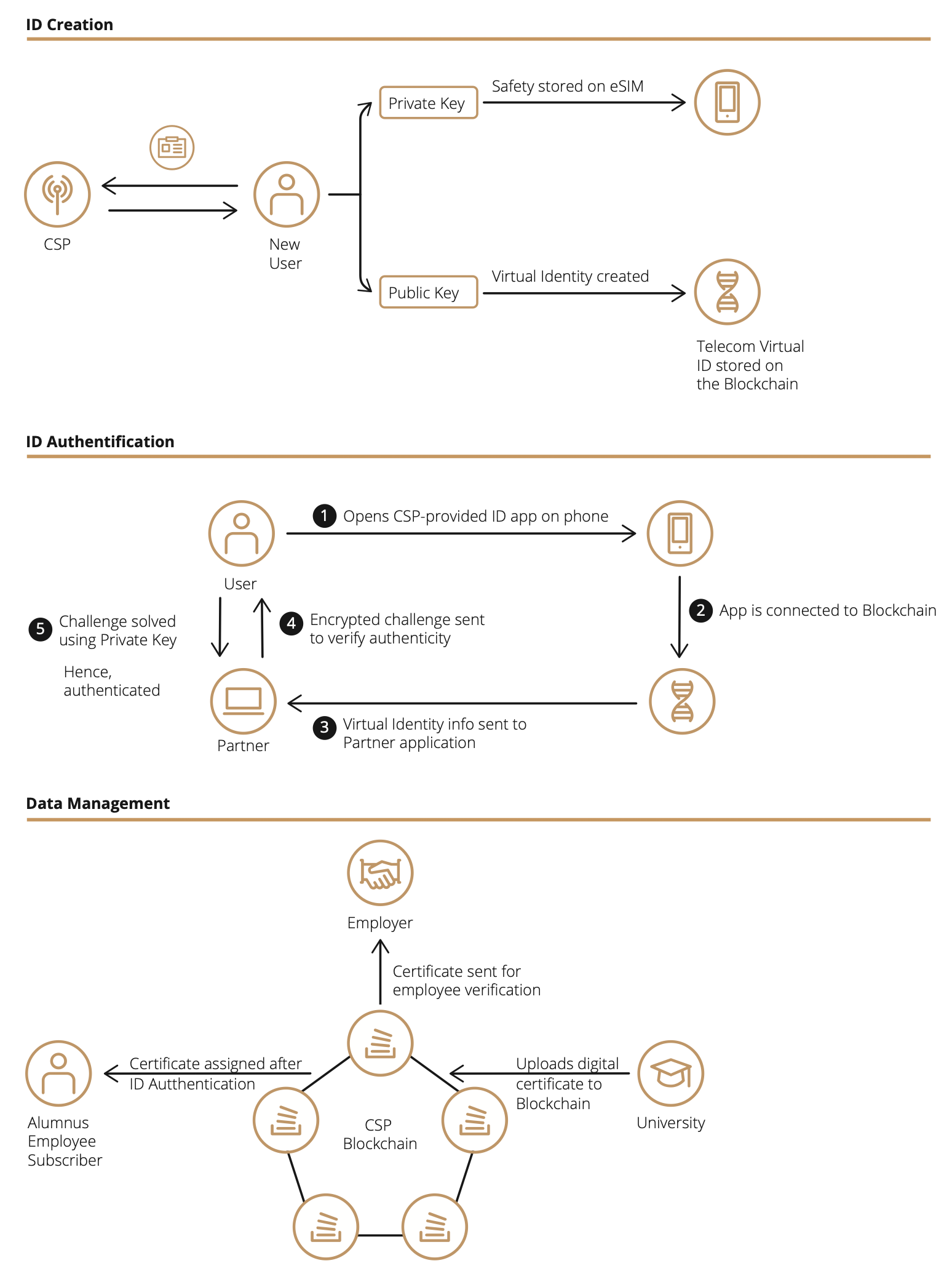
When a subscriber opens an account, the Service Provider creates a digital identity. The private key associated with this identity is securely stored on the SIM. The CSP creates a virtual identity, using the public key of the digital identity and adds a series of standard fields (name, address, etc.). It then embeds a digital signature using its private key and a pointer to this virtual identity, together with the necessary descriptors, and is added to the blockchain.
If the subscriber now visits a partner website, e.g. an e-commerce site, the site will need to know their identity and will launch the application on their cellphone to provide them with a copy of the blockchain ledger entry. The site, to identify the subscriber, takes the public key from the virtual identity, encrypts a challenge and sends it to the application which, having the associated private key, decrypts it and responds. Now the e-commerce site can easily generate an e-commerce virtual identity associated with the user, which is then stored in the ledger.
The next time the subscriber visits the same e-commerce site, they are authenticated through the same mechanism. Moreover, the ledger already contains the history of their transactions and therefore knows their preferences, allowing them to interact with the suggestion engines.
The virtual identity generated by the Communication Service Provider can therefore be used to create virtual identities for various e-commerce sites, such as a virtual identity for a travel site, which does not need to know all the details of the subscriber's identity, as is the case now, but only those that are relevant (such as the address) and add other attributes (such as the preferred mode of travel). The possibilities of such management are endless, the only by the number of partner service providers.
Advantages:
Cost savings compared to traditional IDM software
New revenue from providing identity-as-a-service solutions to partners
Increased ease of use for subscribers
Forming a protected ecosystem for partners
USE 3#: READY FOR 5G
Fulfilling the 5G promise requires ubiquitous access across various networks, heterogeneous nodes and different access mechanisms. Selecting the fastest node for each user or machine will therefore be a central challenge, and the application of blockchain can give rise to a new generation of access mechanisms ideal for building 5G networks.
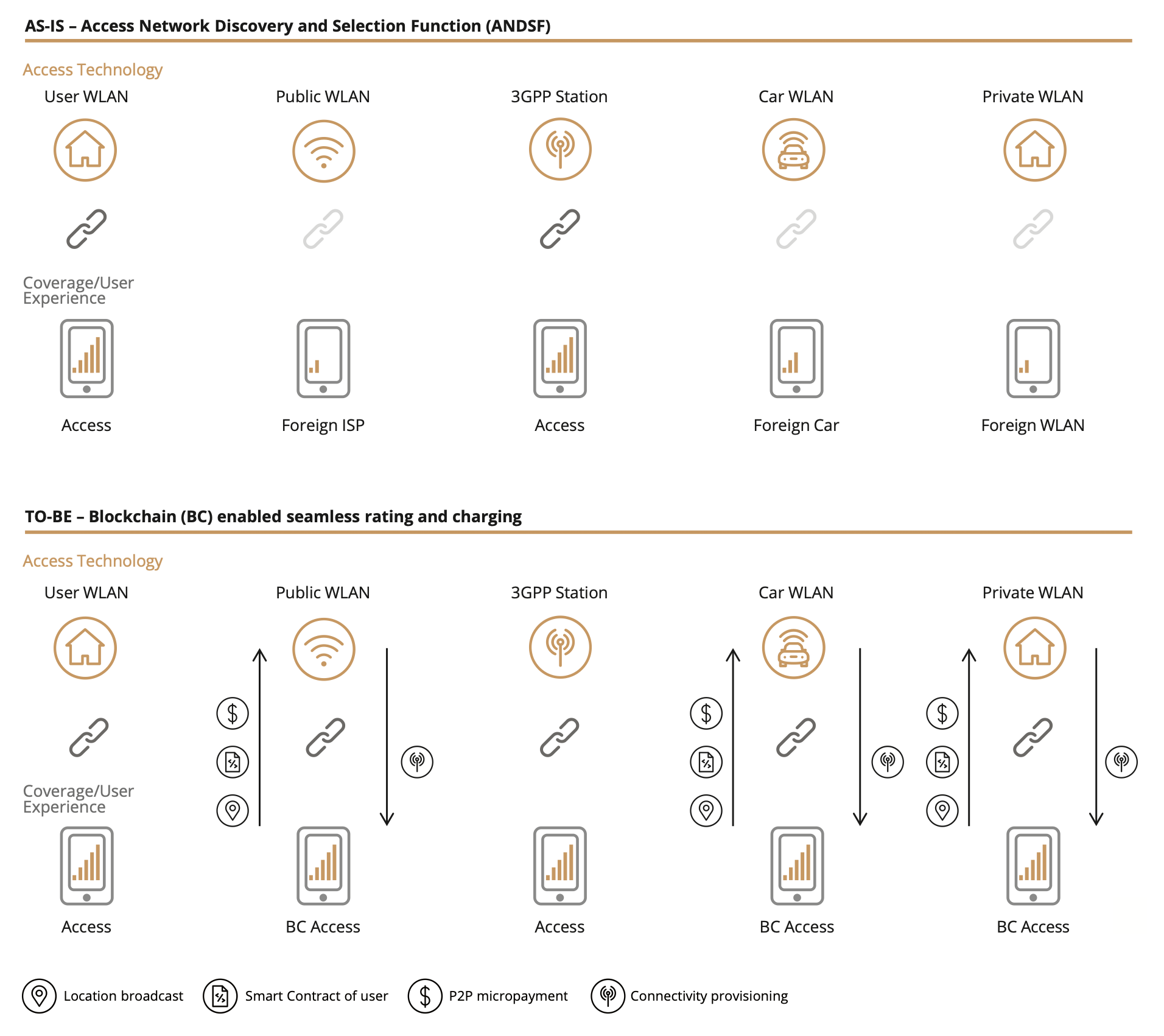
Current situation - ANDSF (Access Network Discovery and Selection Function) oversees the connection of the device with networks, such as Wi-Fi, that are available nearby. This is done with a centralized system in a client-server model, exchanging information about the device and the network, such as its location, supported interfaces and type of access technology. This causes delays and prevents a continuous, real-time flow between the access networks and the device.
The blockchain solution - 3GPP (LTE, GPRS) and non-3GPP (WIMAX, WLAN, Wi-Fi) access networks in a given area can be networked via a blockchain where each access point (Wi-Fi router, SP cell tower, etc.) can serve as a network node that controls the devices. The rules and agreements between the various networks providing access are encoded as dynamic smart contracts, and each time the device transmits its location, the access node that can best provide the service is called upon to do so.
This also allows for seamless and transparent pricing of all services between the various access nodes. If, for example, a WLAN in an office or home network has provided access to another device, then it will receive a reduction in the invoice amount.
Advantages
Faster and more secure connection
Instant monetization of various types of connection
Geolocated connection prices, based on supply and demand in the area
Use of idle capacity to carry non-priority traffic
Last updated